
About the Author
Abdijabar Yussuf Mohamed is a graduate of the Schwarzman Scholars Program in Beijing, China where he obtained his Masters in Global Affairs. Previously, he obtained a Bachelor’s degree in Computer Science from Middlebury College in Vermont, USA. As a Middlebury undergraduate, he was a Kathryn Davis Fellow for Peace & an exchange/associate student at Keble College, Oxford University in the U.K. He previously worked as Artificial Intelligence (AI) policy researcher and cybersecurity engineer. He currently researches the intersection between cybersecurity and public policy. His research interests include cybersecurity and cyber policy; AI & Data Science; Sino-Horn of Africa (HoA) relations; data-based (empirical) study of political violence in the Somali Region of Ethiopia.
Abstract
This article attempts to investigate Ethiopia’s cyber prowess relative to Egypt’s and, albeit to a lesser extent, that of Sudan. Of the three countries, evidence shows Egypt as the nation, among the three, has the superior cybersecurity regime. Ethiopia is ahead of Sudan but falls significantly behind Egypt. Additionally, Egypt has a National Cyber Strategy while Ethiopia and Sudan are yet to adopt robust and sound cybersecurity strategies that advance multi-stakeholder collaboration in the security, public, and private sectors. Additionally, Egyptian elite ethical hacker teams are ahead of Ethiopian and Sudanese ethical hackers in the international “cyber Olympics”. This article concludes with policy recommendations for building a cyber-resilient Ethiopia in which the national critical infrastructures such as the Grand Ethiopian Renaissance Dam (GERD) are protected from foreign cyberattacks.
In part I of“The Grand Ethiopian Renaissance Dam (GERD) as an African Cyberwarfare Front: A Simplified Cyber Attack Scenario & Some Plausible Cyber Attack Consequences”, this article illustrated what a simplified cyberattack scenario on the dam’s command & control (C2) involves and the plausible cyber-physical impacts of a cyberattack on the riverine Benishgul Gumuz Region (BGR) communities and the power grid system. These consequences include devastating power outages, future loss of life due to water poisoning, and reduction of the dam’s computer infrastructures to a global cybercrime station for local and international cybercrime syndicates. Part II will focus on assessing Ethiopia’s cyber capabilities vis-à-vis Egypt and, to a lesser extent, Sudan. After a brief discussion of a simple methodology & limitations, this article provides a discussion on the Global Cybersecurity Index (GCI) ranking of the three countries.
1. Methodology & Limitations
This is an underinvestigated topic and, as a result, there is little previous body of work upon which to build. Due to limiting legal and security reasons, first-hand data on the full extent of each of these countries’ cyber talent pools. Such data falls into the realm of classified intelligence world and it is not my intention as an “objectivity-seeking researcher” to even attempt to seek data that could be, in any shape or form, construed to undermine the respective national security laws that limit access to such critical data. Notwithstanding the dearth of first-hand data, there are useful talent data availed by the GCI ranking and CyberTalents, an independent platform that competitively nurtures global cybersecurity talent through organizing an annual national and regional Capture the Flag (CTF) competition. A CTF in computer security is a competitive exercise in which individuals and teams compete to find “flags” that are secretly obscured in deliberately vulnerable programs or websites. It is a way to determine expertise in hacking within the confines of the law. CyberTalents provides Jeopardy-style CTFs in which competing teams are presented with several challenges of varying complexity levels. The challenges are drawn from ethical hacking categories including, but not limited to, network security, web security, digital forensics, and reverse engineering. Teams can either compete independently or collaborate to form a national team.
2. Commitment to National Cyber Strategy: Egypt and Ethiopia
There are many tools for assessing a country’s commitment level to cybersecurity. This article will refer to the GCI, arguably the most reliable assessment tool for understanding how much emphasis a given nation places on advancing cybersecurity. The GCI is computed by the International Telecommunication Union (ITU), the specialized United Nations (UN) agency responsible for matters pertaining to information and communication technologies, to assess the level of commitment to cyber development of its 193 member states and the State of Palestine. First launched in 2015 and rooted in ITU’s Global Cybersecurity Agenda, the GCI is based on five pillars that determine the intrinsic building blocks of a national cybersecurity culture: legal, technical, organizational, cooperation, and capacity-building measures.
According to the 2021 GCI index, Egypt is one of the cyber powerhouses in the Global South. In global rankings, Egypt scored 95.48% and claimed position 23 out of 182 surveyed countries. In the same year, Sudan scored 35.03% (corresponding to position 102 out of the 182 surveyed countries) whereas Ethiopia scored a dismal 27.74% and position 115 out of the 182 surveyed countries. There are, however, other regional rankings for the Middle East and Africa (MENA) and Africa that respectively included and omitted Egypt.
Given the vastness of the five pillars of the GCI, this article will use two key considerations as our yardstick: national cyber strategy and technical readiness, to fully understand how Ethiopia’s cyber capabilities compare to the two riparian downstream states of Egypt and Sudan
3. National Cyber Strategies: Egypt and Ethiopia
A national cybersecurity strategy (NCSS) refers to a high-level plan of action that is designed with the primary objective of enhancing the security and resilience of a nation’s critical infrastructures. It is essentially a top-down approach that works towards entrenching cybersecurity in critical infrastructures in line with a range of national objectives that are aimed at being attained within the limits of a given timeframe. The next section assesses the national cyber strategies of Egypt and Ethiopia. Due to the sparse availability of reliable cyber strategy information, Sudan is not discussed in this section.
3.1 The Case of Egypt
Egypt has a constitutionally-mandated National Cybersecurity Strategy (2017-2021), an action plan for the period between 2017 and 2021. This strategy involves several key programs that support Egypt’s strategic cybersecurity objectives. It acknowledges the most significant threats and challenges facing the nation’s critical infrastructures – specifically the energy sector, the information communication technologies (ICT) sector, the transportation sector, the health sector, etc. To achieve the security of these critical infrastructures, the strategy greatly emphasizes the distribution of roles among the various government agencies, businesses, civil society, and the private sector. To implement this strategy, Egypt has the Egypt Supreme Cybersecurity Council (ESCC). Developed under the auspices of the Ministry of Communications and Information Technologies (MCIT), ESCC reports to the cabinet and MCIT. It is made up of key stakeholders involved in national critical infrastructure management including the concerned government agencies, professional experts from the private sector, educational institutions, think tanks, and research scholars. The ESCC is expected to update the strategy and shepherd coordinated efforts aimed at safeguarding the national critical infrastructure from internal and external cyberattacks(National Cybersecurity Strategy 2017-2021, 2017).
3.2 The Ethiopian Case
For a very long time, Ethiopia has been trailing its peer nations in technological development. Since the 2006 creation of the Information Network Security Agency (INSA), the Ethiopian government has accorded special attention to cybersecurity policy. Since then, the government of Ethiopia approved two key proclamations – the 808-2013 and 1072-2018. As a result of these proclamations, in 2011, Ethiopia formulated a cyber policy. This policy is still under review and the nation lacks a comprehensive national cybersecurity strategy that guides coordinated efforts at combatting cyberattacks. In addition to the lack of political will to implement a national cybersecurity policy and implementing mechanism, there are two major challenges that the nation faces. The first one is a lack of awareness among the citizenry on what cybersecurity entails and its significance to the nation’s critical infrastructures. Second, is the lack of consideration of the international ISO 27001 cybersecurity standards, the international standard for information security (Markos, 2022).
4. CTF Cyber Supremacy Battle: Egypt, Ethiopia, and Sudan
One way of measuring a country’s cyber power is by scrutinizing the existing cyber talent. Because it is the cyber talent that undergirds a nation’s cyber offensive and defensive capabilities, it is worthwhile to comparatively analyze how that given country compares to its potential digital battle enemies. In this case, we are interested in fathoming how the existing Ethiopian cybersecurity talent compares to those of Egypt and Sudan.
CyberTalents previously organized national CTFs for Egypt and Sudan but Ethiopia had its first national CTF (organized by CyberTalents) in 2020. Given that the 2022 competitions are yet to be held, we considered the available CTF data for 2020 and 2021. As indicated in tables 1 and 2 below, Egypt is ahead of both Sudan and Ethiopia in both participation & winning teams. In 2020, 40 Egyptian teams signed up to compete, 34 of whom successfully solved some of the challenges. In the same year and competition, Ethiopia fielded 37 teams. Out of the 37 teams, 21 teams won points.
Sudan, on the other hand, had 23 participating teams. Only 7 of the Sudanese teams won points.
Similarly, in 2021, Egypt had 102 participating teams and 66 winning teams; Ethiopia had 27 teams and 14 winning teams; Sudan had 16 teams with only 8 of the teams emerging as winners. Comparing the statistics of the two years, notice that Egypt’s participating and subsequently winning teams dramatically improved. In 2021, Egypt had 62 more participating teams and 32 more winning teams than in the year 2020. Contrarily, Ethiopia’s participating teams dropped by 10 and as a result, the previous year’s (2020) winning teams declined by 7. Similar to Ethiopia’s dismal performance in 2021, Sudan had 7 participating teams less than in the year 2020 and 1 more winning team than 2020. In both years, all three countries tied in high-level accolades (gold, silver, and bronze). Hence, these awards are not differentiating factors.
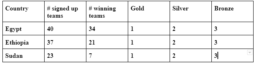
Table 1: The 2020 National CTF competitions data for Egypt, Ethiopia and Sudan
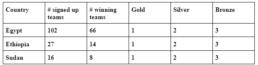
Table 2: The 2021 National CTF competitions data for Egypt, Ethiopia and Sudan
Going by the tabular data above, Egypt boasts of a more active and robust cyber talent than both Ethiopia and Sudan. Coupled with the individual teams’ points for the three cases, we can conclude that Egypt is the cyber talent superpower among the three, followed by Ethiopia and lastly Sudan.
4.1 Tri-Nation CyberTalent CTF Competition Visuals
More self-explanatory details of the team pseudonyms, member pseudonyms, team leaders, specific winning time, points, award levels, etc. are demonstrated in figures 1-6 below.
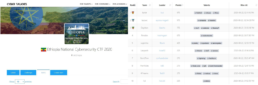
Image 1: Ethiopia National Cybersecurity CTF 20204
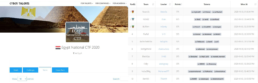
Image 2: Egypt National CTF 20205
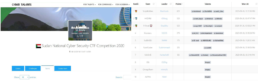
Image 3: Sudan National Cybersecurity CTF Competition 20206
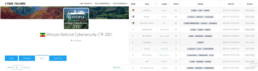
Image 4: Ethiopia National Cybersecurity CTF 20217
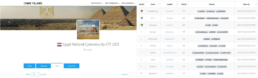
Image 5: Egypt National Cybersecurity CTF 20218
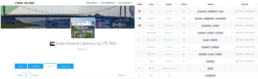
Image 6: Sudan National Cybersecurity CTF 20219
5. Conclusion and Policy Recommendations
Based on the aforementioned findings from the previous sections, one can conclude that compared to Ethiopia, Egypt is a relative cyber power.
While Sudan is a close competitor of Ethiopia in cyberspace, it does not outperform Ethiopia. Egypt’s cyber capabilities in combination with Sudan’s could mean devastating outcomes for Ethiopia in the event that these two countries collaborate in cyber operations against Ethiopia.
Such a scenario can occur if an international battle over the GERD extends beyond the domains of air and land to incorporate belligerent actions in the cyber realm. Bearing this in mind, it behooves Ethiopia to adopt evidence-driven policies that facilitate the following:
- (a) Quicken the process of adopting a comprehensive national cyber strategy that can protect the national critical infrastructures such as the GERD;
- (b) Create an Ethiopian Cyber Command, an organization composed of professional cybersecurity experts that can enhance Arat Kilo’s capability to & authority to guide and control cyberspace operations for strategic purposes;
- (c) Create a Cyber War Studies Program with experts that conduct research in cyber war simulation, cyber war games and defensive technical posture for the protection of the national critical infrastructures;
- (d) Provide support to cybersecurity & cyberwarfare researchers at both public and private universities;
- (f) Integrate a cybersecurity education into the national and regional curricula. Egypt enjoys a democratized higher education that cheaply provides cybersecurity education;
- (g) Provide support for cybersecurity hackathons, conferences, and journals at Ethiopian universities and colleges.
References
- National Cybersecurity Strategies. (n.d.). [Topic]. ENISA. Retrieved September 2, 2022, from https://www.enisa.europa.eu/topics/national-cyber-security-strategies
- Markos, Y. (2022). Cyber Security Challenges that Affect Ethiopia’s National Security. Available at SSRN 4190146
- Mohamed, A. The Grand Ethiopian Renaissance Dam (GERD) as an African Cyberwarfare Front – Horn Review. (August 11, 2022). Retrieved September 2, 2022, from https://hornreview.org/the-grand-ethiopian-renaissance-dam-gerd-as-an-african-cyberwarfare-front/
- Egyptian Supreme Council. (2017). National Cybersecurity Strategy 2017-2021. https://www.mcit.gov.eg/Upcont/Documents/Publications_12122018000_EN_National_Cybersecurity_Strategy_2017_2021.pdf